Galveston Capital Tourism And Marketing: 10 Historical Facts You Probably Don't Know About Galveston
As you may already know, Galveston's rich history is one of the many things that makes us a one-of-a-kind destination. From the spectacular Victorian homes to the wonderful people whom have molded Galveston in to what it is today, there is just so much to learn and discover. Here are 10 historical facts about Galveston that you have probably never heard before:
Number 1, Galveston is the home of the inventor of condensed milk.
Gail Borden was named Galveston’s first customs inspector in 1837. Borden would later achieve fame by inventing condensed milk.

Number 2, Galveston is home to Texas' first bakery.
Irish immigrant Christopher Fox opened a bakery in Galveston in 1838. It was the first bakery in the State of Texas.

Number 3, Galveston was once the leading port of Texas.
In 1842, Galveston received the first cotton press in Texas. By 1899 Galveston was the world's foremost cotton port and the fifth most important port in the United States.

Number 4, Galveston was the first city in Texas with light.
Galveston was the first city in Texas to have gas lights (1856) and later the first city to have electric lights (1883).

Number 5, Galveston is home to Texas' first opera house.
The first opera house in Texas opened in Galveston in 1870. It was on the corner of Tremont and Market Streets. Below are past and present images of Galveston opera houses.

Number 6, Galveston had the first telephone in Texas.
The first telephone in Texas was installed in Galveston in 1878. It was installed in the office of Colonel Belo, founder of the Galveston Daily News, the oldest surviving newspaper in Texas, founded in 1842.
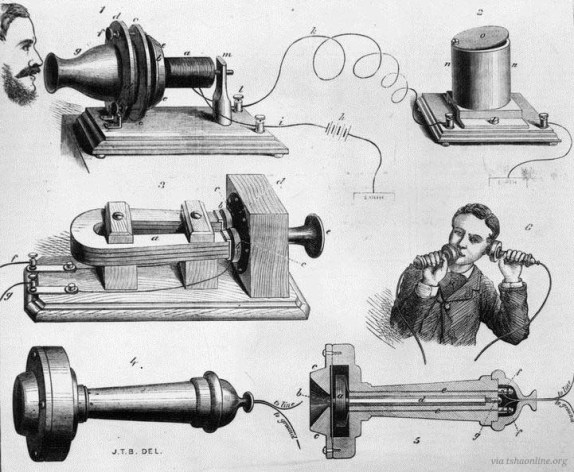
Number 7, Galveston is home to the oldest medical college, now UTMB.
The oldest medical college in Texas opened in Galveston in 1891 followed by the first school for nurses in 1894. Originally known as the Texas Medical College, today it is known as the University of Texas Medical Branch (UTMB).

Number 8, prior to the 1900 Storm, Galveston was the 2nd richest city in US.
On the night of the Great Storm of 1900, Galveston was the second richest city per capita in all of the United States. The only city with more wealth than Galveston was Newport, Rhode Island.

Number 9, Galveston was raised in grade after the 1900 Storm.
After the Great Storm of 1900, a seawall was constructed to protect the city from future storm surges. After construction of the seawall was completed, 500 blocks behind the seawall were raised to even the grade. The task took eight years to complete.

Number 10, Historic Ashton Villa's fence is mostly underground.
Half of Ashton Villa’s historic iron fence is underground. Set into concrete when installed in 1859, the Brown family allowed half of it to be buried during the grade-raising. The gates and newel posts were removed and then reinstalled once the grade was raised so that they could maintain function.

Online Fraud Detection, Cyber Security: Cerber Surpasses Locky to Become Dominant Ransomware Menace

Ransomware-as-a-Service is a hit with the tech illiterate
Cerber eclipsed Locky as the most common ransomware pathogen doing the rounds in the first three months of 2017.
Cerber's control of the cybercrime market rose from 70 per cent market share in January to 87 per cent in March, according to the latest cybercrime tactics report by Malwarebytes Lab.
The success of Cerber is down to its features (robust encryption, offline encryption etc) combined with the adoption of a Ransomware-as-a-Service business model, whereby the ransomware can be modified or leased. "It's also very easy for non-technical criminals to get their hands on a customised version of the ransomware," Malwarebytes reports.
Malwarebytes' findings follow reports from Microsoft that Cerber was topping its Windows 10 ransomware chart.
By contrast, the Locky ransomware (last year's number one) has dropped off the map, likely due to a switch in tactics by the cybercrooks behind the Necurs spam botnet. No new versions of Locky have appeared throughout the year to date, Malwarebytes reports.
Looking beyond Windows, the Mac threat landscape saw a surge of new malware and backdoors in Q1 2017, including a new ransomware (FindZip). Elsewhere two Android nasties – HiddenAds.lck, which locks the device and prevents the removal of an ad slinging nuisance, and Jisut, a mobile ransomware family – have been causing all sorts of problems, according to Malwarebytes.
The cybersecurity firm has built up a solid reputation for exposing the operations of tech support scammers. This form of fraud normally starts with a pop-up ad or phone call claiming that a prospective mark's machine is infected or underperforming. Once victims respond, the scammer’s use a variety of social engineering tricks to coax victims into installing ineffective crudware or subscribing the worthless (or often damaging) services.
Tech support scammers, finding difficulty working with North American payment processors, have begun accepting alternate forms of payment, such as Apple gift cards and Bitcoin, it reports. Some scammer groups have started to scam each other. ®
Plan a Meeting by Galveston Capital Tourism and Marketing Review Singapore Island Hotels

If the views from your meeting space consist of traffic, concrete or other buildings, the answer to your problem is simple. It’s island time!
Leave the stiff and boring behind for the excitement of Galveston Island’s beachfront facilities in one of Texas's top tourism destinations.
Located just 50 minutes from Houston, this 32-mile-long island offers more than 5,000 sleeping rooms, replenished beaches and a variety of world-class attractions to make your next meeting far from ordinary. And, if you’re on a budget, you can join the more than 5 million visitors that flock to Galveston annually to experience the laidback lifestyle of a seaside city without the high price tag of most beach destinations.
Your first step? Discover all the in-kind and cash incentives for which you may qualify! Contact the Galveston Island Convention & Visitors Bureau to get the best head start possible on planning a successful, stress-free meeting.
#LoveGalveston Photo Contest - A Chance to Win Cash, and Be the Face of Galveston
There’s nothing like spending “island time” with your family, taking in the Galveston coast while making memories you’ll cherish for a lifetime. While your memories may be priceless, capturing them in a photograph could lead to some extra bonuses.
First of 1 Million Cubic Yards of Sand Has Been Pumped Onto the Beach
The first of 1 million cubic yards of sand has been pumped onto the beach in a $19 million project to replenish over 3.5 miles of beach along Galveston's seawall.
Group Activities Beckon & Abound on Galveston Island
If you’re looking for group activities, there’s plenty of things to on our charming little island.
Planning a Meeting? Why Not in Galveston?
Most visitors come to Galveston to relax on the beaches, stroll the Strand, maybe visit museums and to dine at some of the island’s most popular restaurants. Yet despite it being a vacation destination, Galveston is also a great place to hold meetings.
Dellanera RV Park Offers Hook-Up Sites Right on the Beach
Have you ever dreamed of having a home right on the beach? That’s what those visiting the island in an RV can have – so to speak.
The Galveston Island Pass is your Ticket to Island Adventures and Savings Too
Whether you’d like to kayak on Galveston Bay, visit the Railroad Museum or watch the sharks at Moody Gardens Aquarium Pyramid, the Galveston Island Pass is your ticket to island adventures.
Major Galveston Beach Expansion Now Underway
A major beach expansion is now underway in Galveston, representing the largest sand nourishment project to take place on the Texas Gulf Coast this summer.
Galveston Capital Tourism and Marketing Review Singapore Hope you experience this “causeway cure” where flip-flops replace dress shoes and the scenery.
Join a group thrilled you have decided to explore Galveston Island.
Cyber Security: Protecting Seniors Online from Scams, Hacks and Tax Fraud
 The vast majority of seniors today are using the Internet at least once a week to check email, pay bills online and keep in touch via social media. But all that time online puts them at risk for scams and hacks, such as tax fraud.
The vast majority of seniors today are using the Internet at least once a week to check email, pay bills online and keep in touch via social media. But all that time online puts them at risk for scams and hacks, such as tax fraud.
In fact, a new survey by Home Instead, Inc., franchisor of the Home Instead Senior Care network, found that 67 percent of surveyed older adults have been the victim of an online scam or hack.
Encouraging seniors to practice cyber security can go a long way toward protecting their identity and sensitive financial information. Home Instead collaborated with the National Cyber Security Alliance to create Protect Seniors Online, available at www.ProtectSeniorsOnline.com, a free resource that educates older adults about cybersecurity. Here, seniors can test their cybersecurity skills with the "Can You Spot an Online Scam?" quiz.
Older adults can take the following steps now to protect themselves online:
- Password protect and secure devices, accounts. Lock all devices (including computers, tablets and smartphones) with secure passwords in case devices are lost or stolen.
- Think before clicking. When faced with an urgent request -- like emails asking for money -- think before clicking or get a second opinion. Clicking on links is often how scammers get personal information. When in doubt, trash an unusual message.
- Share with care. More than half (51 percent) of seniors surveyed by Home Instead use social media to stay connected. Use care when sharing personal information, adjust privacy settings to limit who can see your information, and turn off location sharing.
- Use security software. Install anti-virus and anti-spyware software and program it to run regularly. And be wary of pop-up ads or emails, many of which contain malware that can infect computers.
- Log out. Log out of apps and websites when you are finished. Leaving apps and websites open on computer screens could make you vulnerable to security and privacy risks.
- Recommend support. Older adults who live alone may need help from a trusted source -- such as a family member, tech-savvy friend or professional caregiver --to serve as a second set of eyes.
Southbourne Positive Living Group: Top 5 Tips for Living a More Positive Life

This is a part of Darren Rowse´s writing project “Top 5” over at Problogger.
I´ve mentioned all of these suggestions once or twice before but really like them since they are very useful if you want to improve your life.
And, besides, I´d bet that few besides me have read the whole archive anyway.
- Appreciate, appreciate, appreciate!
People often want appreciation from others. It can become a craving need. Instead, start to appreciate everything around you, such as:
– The sunshine and the weather.
– Your food.
– Your health.
– The people around you. Your friends, family, co-workers and just about anyone walking down the street.
– A good TV-show, a movie or a song.
– A good conversation.
– Your roof and your house.
– All the great things you can find online.
– Yourself. If you just look there is a lot to appreciate about yourself.
It’s a quick way to turn a sour mood into a more positive and useful one. Just try if for a minute and see how it changes how you feel. And it’s a win/win solution. You feel great because you are appreciating your world and the people you appreciate feel great too because they feel appreciated.
And since the Law of Reciprocity is strong they’ll often start to appreciate you too thereby starting a growing upward spiral of positive thoughts and emotions.
But don’t focus too much on that though. Just focus on appreciating your world and let rest take care of itself.
One way to use appreciation to get a good start in the morning is by asking yourself a set of questions.
Read more about that in How to Start Your Day in a Better Way.
- Focus on what you want, not on what you don´t want
The more I do this, the more I discover that it is so key in improving your life. It´s simply filling your life and time with more of what you want.
The thing is that it is very easy to fall into a habit of focusing your thoughts on what you don´t want rather than what you want. If you do that then it will be hard to get what you want in life.
If you want to improve your finances then focus on having a great financial situation rather than your lack of money and your debts. If you want a new relationship then focus on meeting a lot of new people and forming great relationships rather than focusing on your loneliness and your lack. If you don’t then you’ll miss many opportunities that you mind just blocks out since it’s focused on your lack.
But if you do then opportunities will suddenly start to pop out of all that stimuli that is your world. Your mind can mostly just see what you focus it on. So focus on what you want in life.
Read more about this suggestion, the Reticular Activating System and The Law of Attraction in this article.
- Educate and explore yourself
Self-education can be a great help to live a better life. Read great books on the areas of your life you want to improve. Maybe it’s it your financial situation or your health. Or maybe it’s your relationships.
Ask people with more success in that area than you what they did to improve. If you have a problem in your life, most likely a lot of people have had that problem the last few thousand years. And, at least one of them – or more likely a few – has written down how they solved that problem.
This is also a great way to get to know yourself better and understand why you think, feel and do – or don´t do – the things you do. And knowing yourself better – and other people too, since we share so much that make us alike – is pretty useful if you want to improve your life and lives of other’s too.
Feed your mind daily – or weekly – with great solutions and inspirational and useful information. Some really great sources I have found so far are listed in Recommended Personal Development Products.
- Take a lot of action in your life
Yeah, this one’s maybe easier said than done. But there is also good information on how to go about it and it’s a great way to improve your life.
“Just do it!” is a nice slogan. But if you feel like you really can’t do what you want then it will probably not be too helpful. If you feel that fear is holding you back from doing something then there are good and practical solutions that has been used throughout hundreds or thousands of years.
One of my favorites is taking small steps and confronts your fear little by little and thereby creating a momentum that lets you move on to the next step. Another is learning to surrender and accept the now. For more on that suggestion and other strategies to reduce fear (such as redefining failure), check out 5 Life-Changing Keys to Overcoming Your Fear.
Other suggestions to remove or reduce blocks that stop you from taking action is to explore some techniques – such as guided meditations – that can help create a forward momentum within you. More on that can be found in How to Move beyond Being a Self-Help Junkie.
Procrastination is of course also a big problem when trying to take action and getting things done. My favourite technique to beat it so far is using the “Get around to it” Paraliminal. Paraliminals are a sort of guided meditations produced by Learning Strategies. 7 other free and useful methods to beat this problem can found in this article (and you can find one more here).
- Improve your social skills
So much of the happiness, value and fun in life come from interactions and relationships with other people. Improving those interactions and your communication skills can greatly improve your life. And – as a bonus – as you focus your attention more outward, toward other people instead of focusing inward much of the negative feelings that can come through overanalyzing and feeling self-conscious mostly just disappear. You just are. And that’s a pretty good feeling state to be and communicate in.
Southbourne Positive Living Group (SPLG) meets on the last Wednesday of the month (excluding holidays).
Join a group of like-minded people and rediscover the purpose and meaning of your life.
Cyber Security: Calgary fraud cases jumps dramatically during grim economic year

Fraud crimes in Calgary during the first three quarters of 2016 were up nearly 28 per cent over the previous year, a spike that’s seen city police alter their approach to combating it.
Up until the end of last September, fraud-related crimes were up 27.6 per cent over the same period of 2015 and during that month last fall, increased by 59 per cent, say city police statistics.
During that period of 2016, police cleared 30.7 per cent of those cases.
Those numbers come at a time when Calgarians’ finances are still reeling from a recession amid a prolonged oil and gas slump.
There’s been a definite increase in fraud crime in the city, driven largely by Internet-based scams, said Staff Sgt. Cory Dayley, head of the city police cyber forensics unit.
“Absolutely it’s increasing — it’s a very easy message for someone to get out to a large number of victims, put a fish hook out and see how people respond,” he said.
“It’s a very lucrative platform to pursue their criminal ways.”
Because of that, Calgary police last fall merged its 12-officer cyber investigation unit into its integrated fraud team.
“It’s so we have a much more in-depth response to people victimized online,” said Dayley.
“We want to know what that landscape is.”
Another reason for the ballooning number of fraud offences is the greater willingness of victims to come forward and the CPS’s improved reporting system.
Police have also spent more resources publicizing the problem, partly through more charges profiled by the media, he added.
“We’re trying to really get out there, get people to be aware, to be their own best line of defence,” said Dayley.
“People have got to protect their own information, watch their bank accounts.”
Coalition Against Insurance Fraud: Lemons or lemonade?

First P2P insurer says it will slash fraud costs
Do insurance consumers have a thirst to buy policies using their smartphones? Will they be less fraud-prone knowing some of their excess premiums get donated to charity? And will the prospects of quick claim cash motivate them to switch carriers?
One new insurance startup is betting yes, offering to quench that thirst.
Lemonade, the first so-called peer-to-peer insurance company, debuted this week to much fanfare.
Started by technology entrepreneurs, the company is targeting smartphone users by offering ease-of-service transitions and cheap prices on homeowners and renters coverage.
Lemonade says most insurance “sucks” (their words) because insurers hassle claimants, are bloated and make too much profit. And thus, claimants are more likely to file inflated or fake claims.
The company says it will undercut traditional insurers by using streamlined, tech-oriented transactions and reduced fraud costs. In an interview this week, Lemonade president Shai Wininger said:
“With insurance, over 90 percent of the fraud is perpetrated by supposedly normal upstanding citizens like you and me. So what is about insurance that brings out the devil in us? Why is it that when it comes to insurance, we feel entitled to break the law?”
Research suggests consumers are less likely to defraud a company they feel good about. Customers designate a favorite charity to receive their share of company profits at the end of the year, if there are any.
Call me skeptical, but I doubt Lemonade’s approach will make that much difference in policy pricing.
Still, Millennials who love transacting business on their cellphones and are socially conscious should be drawn to this model. It will be interesting to see if Lemonade has a magic formula to reduce fraud. We’ll be watching to see if this new player leaves a sweet or sour taste in the mouths of its customers.
About the author: Dennis Jay is executive director of the Coalition Against Insurance Fraud.
Socials @ Power Kids Gym by New Mothers' Support Group

We have arranged a regular monthly social at Power Kids Gym (formerly JWT) UE Square. This is a soft play gym with a sprung floor and lots of soft play equipment, ideal for all ages.
You can register your interest in attending this event via the NMSG Meetup Group
- Please note that the maximum number of children is 30 and the cost is $5 per child.
- Socks or bare feet only please.
- There will be no Pediatrician attending this event.
- Please note, due to the popularity of this venue, we have started a first come / first served system as there is a limit to the number of children/adults permitted in Power Kids Gym at any one time.
- Meet-up registration does not guarantee you a place at our regular socials.
- Power Kids Gym is kindly offering our members the following promotion:
- 1x Free Trial Class (worth $42)
- 1x Membership Fee Waived (worth $60)
- Kid’s Night Out at $49 only! (Usual Price $79). Kids’ Night out is our 4 hour Drop your kids off party, filled with some high energy activities, where they will navigate through obstacle courses, create fabulous crafts, have a pizza and go wild with our trainers. Parents enjoy the night out without the kids.
When?
3pm - 4.30pm on the following dates in 2016
8 November
13 December
Where?
Power Kids Gym
81 Clemenceau Avenue
UE Square, #02-12
Singapore 239917
Organiser
Pip Johnson
Anti-Fraud Organization Tokyo, Japan: Contact us
If you are willing to import any product from an exporter in Japan, it is strongly recommend for your own safety to verify any Japanese website or company's status before confirmation of order. To avoid internet fraud DO NOT remit money to any company without your full satisfaction.
Send inquiry for any Japanese company by filling form at below. At the Your Message* area of form, write maximum detail of Japanese company you are inquiring for, such as company name, full address, Website address, and Telephone number. If you are a victim of fraud or phishing scam, write full detail of your communication with so-called company.
Just Released: Keg-Style, Air-Charged, Portable Eyewash by Haws

Introducing the new Haws Model 7603!
Haws model 7603 is a 15-gallon, self-contained portable eyewash and is an ideal, cost-efficient solution for a facility’s ANSI eyewash requirements in locations without access to a continuous potable water source.
The unit provide approximately 10 usable gallons (37.9 liters) of water for effective rinsing of the eyes, face or body and provides a reliable source of safety for the irrigation process.
Additional Features:
- 15 gallon (56.8 L) stainless steel tank
- Protective measures include: air pressure gauge, pressure relief valve, and tire-type air fill valve
- Soft-flo ABS plastic anti-surge eyewash heads with integral flow controls
- Measurements: 39-1/2″ (100.3 cm) high, 16″ (40.6 cm) diameter
- Certified Certified by CSA to meet the ANSI Z358.1 Standard for Emergency Eyewash and Shower Equipment
- Optional 8′ Drench Hose, Model 8901B, for face and body irrigation
- Optional Transport Cart, Model 9008, designed to transport stainless steel portable eyewashes
Bacall Conniff and Associates Review: The impact of restaurant business
We can't deny that restaurants now play an important part in our lives. Today's world is always busy and most people want everything to be made as fast as possible, be it a business transaction or searching the recent album release of your favorite artist. Looking or preparing some food is not an exception, that's why we have a lot of restaurants available these days.
Its changes came from little to big changes happened in each sector of the society - from family traditions, industrialization, and change in the whole economic system.
It's amazing how people in the past do everything at their own homes. You will see a lot of plants surrounding their houses and they even raise animals for meat. They are also used to build their own houses, especially those who live in the wilderness.
People continue to improve their lifestyle, thus the birth of towns and cities occurred. Formal education has been introduced along with the removal of the barter-trade system. People learned how to focus on various skills or enterprises to make a living. They also entrust the cooking of their food to an individual or an enterprise that makes good money in doing so.
With restaurants, you can surely save more time and enjoy different cuisines at one place. The success of this business is evident in our current society. A lot of people tend to spend their breakfast, lunch or dinner at restaurants because of their busy schedules since they don't have enough time to cook for themselves.
However, with the massive growth of restaurants, come the fast foods chains which offer foods that are not really healthy to the body if consumed on a regular basis due to the fact that these foods are often high in calories yet offer little or no nutritional value. Because of this, many restaurants now offer fresh alternatives in healthy diets.
If you're a restaurant owner and you need help about the accounting or financing of your business, don't hesitate to contact Bacall Conniff and Associates. Restaurants around the world will surely continue to provide delicious foods to everyone.
Hawkfield Gallery: Folk Art, Furniture
Scrimshaw Jagging Wheel (Bone) - American 19th Century, Bird motif prongs holding the wheel. Provenance Eldreds, Cape Cod- from a Massachusetts collection originating on Nantucket. Condition good. Tight age crack length of handle. Length 5.5"
Totem (Wood) - 20th century. Northwest coast style totem in pine. Raven, frog, bird, and others topped by a whale's tail. Polychrome paint in rich colors. Condition very good. Height 65".
Charles Limbert, Mission Rocker (Wood) - American, Early 21st century. Oak and leather rocker. Stamped under arm. Label on seat cushion #670, Limberts Arts and Crafts, Charles P. Limbert Company. Condition Very good. Height: 42", Depth 30" , Width 29" Other Notes: Charles P. Limbert (1854-1923) and was a contemporary of Gustav Stickley. After learning the furniture business with his father in Akron, Ohio, he established his own furniture factory in 1902 in Grand Rapids, Michigan, designing and building what he termed "Dutch Arts and Crafts Style" furniture.
Three Tier Shelf (Wood)Three Tier Wood Shelf - thought to be sassafras. Good condition. Some chips to shelf faces. Height 29.75", Width 30.25", Depth 6"
Mallard Andiorns - Pair of Cast Iron Mallard Duck Andirons, nice used surface with traces of Polychrome Paint. Very good used condition. ht. 10 3/4, wd. 14 1/4, lg. 19 3/4 in.
Mahogany Checkerboard (Wood) - American late 19th to early 20th century, Painted Mahogany Checker Board. Wells on sides hold replacement turned wood playing pieces, 13.25" x 11"
Polar Dry Sink - Circa 1840 Polar Dry Sink. Lift top over two half-drawers with two paneled cupboard doors below. Good refinished condition. Tight age crack to one door. Height 38 .25", Width 44", Depth 18.25"
Eagle Weathervane (Copper) - Circa 1930 hammered Eagle Weathervane, intended for use on a flagpole or cupola. On wooded base, nice patina, appears to be copper. Condition excellent. 17.5 Long 25" wingspan, 23" High from bottom of base.
We specialize in 20th and 21st century American fine art and folk art, having a particular interest in American impressionism, wildlife bronzes, decorative songbirds, and shore bird decoys. Gallery owner Sally Caverly has over 25 years of experience collecting art. This field experience combines with her B.A degree in marketing, a master's degree in education and work experience as Market Research Division Director of a major publishing house.
Heimdal Online Security: Social Scams The Full Breakdown and Protection Plan
Remember the time when our email inbox was filled with requests to help endangered (and filthy rich) Nigerian princes?
Those scams never died, they just evolved. Attackers improved their tactics and changed the channel.
More people connected to the internet means that cyber criminals just have more potential victims. And when internet users migrate towards the social networks, guess where the attackers will be waiting?
Does this look familiar?
I bet you thought it’s a harmless post. But you could be just one click away from a nasty malware infection.
That’s why we decided to break down social media scams, so you can know what to expect and how to protect yourself.
- Here’s the rundown of what you can learn from this article:
- Core reasons behind scams on social networks
- How scammers take advantage of social networks to make money
- Common tricks you can come across
- Social media scams on Facebook, Instagram, Twitter and more
- Get it done: Must have in-account & on-device security settings
Core reasons behind scams on social networks
- Make more money
Scammers plan most of their scams with one and only goal in mind: money. They will do anything to monetize your actions and your sensitive information.
They trick you to click on a link, download or install something, like or follow a social profile, share something or send it to your friends. They’ll try to gain any type of information from and about you that they can exploit or simply sell to others. They’ll even try to talk you into willingly sending them money.
- Just for fun
However, some of these scams are done just for fun or out of curiosity, to find out if and how something works.
A quick example of a basically harmless scam: you’ve most likely come across at least one chain letter passed on via popular social networks. These are messages that claim that the owners of the network will start charging users or that it will shut down. They will prompt you to forward the message to everyone you know in order to shut down. Others claim that a brand or celebrity will donate money to a charity cause for every share of that message.
These kinds of scams are only social media clutter and noise. But they can also turn malicious very quickly.
How scammers take advantage of social networks to make money
- They trick you into visiting websites and / or clicking on ads
Most websites make money from selling advertisements. The most common type of advertising is based on paying for impressions (page views – how many times did a potential customer view an ad?)
The impressions system is based purely on traffic, on the number of times an ad was displayed to a user while viewing a web page.
The pay-per-click system means that advertisers only pay the website when a user clicks on an ad.
This system can be tricked by generating clicks that don’t come from genuinely interested users, or by hijacking clicks that were intended for a legitimate advertiser.
You may argue that it’s harmless, and that an individual page view or click will only bring scammers a tiny amount of money.
So what if they trick you into clicking on an ad and you thought it’s a completely different thing? Only wasted time, right?
Well, if you start multiplying those few cents from your click with other millions of clicks that they managed to gather, you’ll see that scammers can fraudulently raise serious amounts of money.
This is called “Click fraud” and, according to a report from the Association of National Advertisers, marketers all over the world could lose this year up to $7.2 billion because of it.
It’s also worth noting that 90% of web attacks are delivered through advertising networks.
- They trick you into liking pages, following people, tagging, commenting
This is similar to the previous point.
By making you like a page, follow an account, comment or tag people, scammers will raise the numbers of a social account. They also ensure that the action will appear in your news feed, providing them with access to more people.
Sometimes, this is for the own benefit of the scammers, so they can pretend their account has genuine online influence and then place ads it or even sell it.
Other times, third parties such as brands or companies will buy likes or followers for their social accounts. This way, they’ll be able to better sell their social media accounts; by making advertisers think they have real influence.
I’m just trying to clear how these things work, so I’ll not comment on the ethics of this action, as it’s not the main subject here.
- They trick you into giving them sensitive information
Phishing is the name given to cybercriminals’ attempt to trick you into giving them sensitive information or money.
They will craft a plausible message that seems to come from a social network representative or from one of your online buddies. They will then lead you to a site that appears to be legit, where you’ll be prompted to enter sensitive information.
From name to email address, phone number, home address, social security number, to credit card details, bank account number, passwords, etc. – this kind of information can be used for financial fraud, identity theft, and blackmail and so on. That’s why it’s important to keep in mind that your personal information is as precious as gold and you should do anything to protect it.
Phishing attacks used to happen mostly through emails, but the landscape has changed dramatically over the past years, due to the rapid growth in social networks usage.
How scammers can take advantage of social media for phishing attacks:
– By pretending to be a representative of a social network.
Phishers take their time to create websites that look identical to your favorite social media networks. They also create fake emails or social profiles that seem to belong to genuine representatives of the network.
After they contact you either directly on the network, through private messages, or through emails that seem to be from the social network’s representatives, and they try to trick you to click on a link to: reset your password, reconfirm your account, and confirm that you don’t want your social account to be cancelled and so on.
This kind of information can then be used to access your account and send messages to friends, to further spread the links.
Other times, they can make money by exploiting the personal information they’ve obtained, either by selling it to third parties or by blackmailing you with this repercussion.
– By sending messages that appear to come from a buddy. In those messages, they invite you to click on a link to check out a video or see some disturbing news.
– By finding out essential information about you that will then increase their chances of a spear phishing attack.
Spear phishing is directed at specific companies or individuals, and it’s not as automated as common phishing.
The attackers will take their time to gather all available information about their target, in order to create a highly personalized and believable email.
Last autumn, researchers from the Dell Secure Works Counter Threat Unit identified a network of at least 25 well developed LinkedIn profiles that were part of a social engineering campaign.
Spear phishing requires a bigger effort, but it’s the most effective kind of phishing attack. And with the publicly available information that we voluntarily share on social media, its chances for success will most likely increase in time.
Phishing is also a potential launch ramp for malware, which leads us to… trick nr. 4:
- They trick you into downloading malware
Malware is used as a collective name for malicious software – the type designed to disrupt or damage your data, software or hardware. Viruses, worms, keyloggers, Trojans – all these are just different forms of malware.
Cyber criminals spread malicious software for profit through adware (forced advertising), spyware (stealing your sensitive information) or ransomware(software that encrypts your content, blocks access to your system and demands payment in return for they key that will decrypt your data).
Usually, attackers get malware into your device through a variety of mechanisms that involve exploiting human and technical factors. You can get infected with malicious software just because you thought you were downloading a browser extension, an app or a game.
Examples of harmful apps to steer clear from:
- Apps that claim to let you know who visited your profile
- Apps that claim to enable the Dislike button on Facebook
- Apps that claim to be a virus removal tool that will clean up your computer
- Apps that claim to change the color of your Facebook profile
- Apps that claim to provide you free likes or followers
This kind of applications carries more or less dangerous types of malicious code. Afterwards, your social account will be used to spread the apps to your friends, sending them messages to encourage to download the software as well, thus further propagating itself.
These scripts can also command your profile to like other pages, helping scammers further monetize the con.
- They trick you into spreading chain letters
We’ve mentioned these before. Chain letters are messages that catch your interest by claiming that a social network plans on charging users in the near future or that they will shut down. Chain letters ask you to distribute the message to everyone you know, in order to stop the network from charging money or shutting down.
Other forms of chain letters claim that a brand or celebrity will donate money to a charity cause for every share of that message. Bill Gates and Mark Zuckerberg are usually targeted for this one.
Variations include emotionally extorting you through fake stories of sick kids, false warnings of viruses circulating, monetary rewards, etc.
These letters used to be sent exclusively via email but, nowadays, because of the increasing popularity of social networks, cyber criminals started taking advantage of them and our decreasing attention span.
Chain letters can take the form of a post from an online buddy, or a direct message.
They are generally harmless, but, other times:
- They will ask you to donate money for a charity cause (that’s actually controlled by a cyber criminal).
- They will urge you to download something in order to protect yourself from a virus that is circulating on the web. This can be done either by clicking on a link that redirects you to a phishing site, or by downloading an attachment that contains malware.
Many people have fallen for this kind of stuff and continue to propagate the messages.
Break the chain – report the message (or mark it as spam), delete it and inform the ones who sent them that they are fake.
Common tricks you can come across
Instead of focusing only on highly technical methods, scammers base their attacks on social engineering tactics.
Cyber criminals will cheat, lie, exploit your trust, take advantage of your emotions, curiosity or lack of technological knowledge, trick you to install malware or divulge sensitive information. No trick is off-limits.
It’s important to note that most people won’t even report when they were tricked via social engineering. They realize they were stupid and don’t want to further embarrass themselves. Reporting would benefit everyone involved, so it’s time to get over your mild embarrassment.
Here are a few scenarios that you must pay attention to:
- Shocking news
Shocking news uses something that’s hot right then. It’s something that everyone is talking about in the media and on social networks, such as a terrorist attack or a flight crash. You might expect to see a video or news, but, instead, the link leads to spammy, pop-up filled or malware-laden websites.
“Curiosity killed the cat”.
- Fake celebrity news
Kim Kardashian’s newest bum photos? Bin Laden’s video death? Vanilla Ice dead?
Always a sure way to get clicks from gullible users.
- Emotional extortion
Photos of sick babies or endangered animals that lure you into watching a video or to see news.
- Free stuff
Gift exchanges, free coupons, free trips, free iPhones, free likes or followers, gift cards – basically, free everything.
These scenarios usually take advantage of big brands names: Starbucks, Victoria’s Secret, the Cheesecake Factory. And they come in exchange for other potential ways for the scammer to propagate the con: click here, like and share, tag friends, follow someone, etc.
- Easy money
Remember the Nigerian prince scam, where you’re typically required to send money over so that, in turn, you’ll receive several times more than the originally borrowed sum?
Or the spammy emails that claimed that you won millions of dollars at a lottery or a prize in a competition?
In order to receive the prize, they prompt you to send over some personal identification information and a small fee for post office.
These kind of scams just moved from email to direct messages on social networks. Here’s an example from LinkedIn.
Easy money doesn’t exist. These are usually bogus offers that claim to help you start making thousands and then require a fee for you to get going.
- Urgency
In this category you can fit any message that has urgent requests. “Click here now, confirm here, download this, fill in this, install this” – messages that require your urgent action are usually used in phishing attempts.
Read and Visit us for more information about Social Scams the Full Breakdown and Protection Plan
Cambridge Associates: How can we align our social values with our investing strategy?
Whether you’re a charitable foundation looking to have a direct impact on community programs or a family eager to make investments that align with your personal priorities, you need to consider a few things. How will you define success? What impact will these investments have on the overall risk/return profile of your portfolio? How can you measure the non-financial accomplishments of these investments? Will there be additional resources or Committee time to address MRI-related issues?
Our MRI team of 25 professionals provides research and services that encompass a broad range of strategies, such as positive and negative portfolio screening, microfinance, clean energy and technology, community investments, real assets, bespoke and illiquid impact investments, and program-related investments. And our databases track more than 450 funds that meet various MRI criteria.
We’re spearheading MRI manager due diligence and analysis, creating an infrastructure for the inclusion of MRI managers in our proprietary databases, and publishing research on a variety of MRI topics. Whether you are debating the topic for the first time or you have already adopted a commitment to MRI, we can help you navigate the many policy questions and investment decisions you need to make.
Axia Consultants: Tips for Attending Accounting, CRM, HR & Payroll Exhibitions
To get the most out of an exhibition - plan what you are going to do before, during and after attending. 12 key points / tips are listed below.
Before the exhibition
- Draw up a list of objectives for visiting the exhibition. Define what you wish to achieve eg to get an overview of certain types of software, see the latest software functionality, or to meet certain vendors.
- Plan your visit. Make a shortlist of exhibitors, vendor demonstrations, educational or other sessions you wish to see. Don’t consider spending all day in vendor software demonstrations - they may end up sounding and looking alike and you may end up being totally confused. Plan a balance of visiting stands, meeting vendors, discussing your requirements, as well as attending demonstrations.
- Mark the locations of the stands / demonstrations you wish to see on an exhibition layout planner so you know your way around the exhibition floor and can save time / avoid getting lost when you are there.
- Attending with colleagues can help to determine which software to investigate further. However, plan in advance who is attending, who shall see what and when. Aim to cover all items, with colleagues splitting up to cover different parts of the exhibition.
- Determine how you will get to the exhibition - so that you arrive on time and are able to complete everything. If you are attending for more than one day and need overnight accommodation, book well in advance of the date(s) required.
At the exhibition
- Follow your visit plan. Ensure you cover the areas you wish to see. Don’t get side-tracked once at the exhibition - you can use any time left over at the end to visit other stands which look interesting.
- If attending with colleagues - use the opportunity to quickly obtain a large amount of information and to network / create new contacts for later use. Work the exhibition - don’t just stay together or treat as a day out of the office!
- Take a copy of your outline system requirements* with you - to refer to and / or raise key points with vendors / exhibitors.
- Take plenty of business cards - to hand out to exhibitors and to save filling in their forms with your details.
- Take a pen and small note pad for jotting down key items, demonstration notes, points of interest, contacts etc.
- Attending exhibitions can be tiring. They can be hot (particularly in poorly ventilated demonstration rooms) and you may do a lot of walking. Be prepared - wear comfortable clothing and take regular refreshments throughout the day.
After the exhibition
- Review the information you have obtained and write up notes / ideas as applicable. Discuss with colleagues. Then determine which software vendors you wish to follow up on and investigate further.
* If you have yet to complete your system requirements, see the Accounting, BI, CRM, HR, Payroll and HR+Payroll RFI/RFP Templates - which can help you quickly identify and specify your system requirements.
Human Capital Alliance: Professionals Service Providers Lay Stress on Stronger Relationships
Editor: In 2004, Edwin Sim established Human Capital Alliance, Thailand’s Premier Executive Search & Senior Advisory Firm. Between 1997-2003, Edwin Sim was Managing Partner of Korn Ferry Thailand. This article was first published by the Nation in July 2001.
K I Woo looks at how transaction-oriented professional service providers are shifting their focus to building client relationships.
Coming out of the financial crisis, Asia ’s multinational professional service providers are changing their strategic focus.
During the economic boom, major international law, accounting, architectural and engineering, management consulting and executive recruitment firms only had to sit in their offices while their phones rang off the hook. They spent most of their time deciding which potential clients to call back.
As the crisis tightly gripped the country, many professional service providers switched gears and became restructuring specialists. Forced to restructure or go out of business, clients continued to run to them. Business for professional service providers continued to boom during the crisis. They ainly focused on handling short engagements as their clients fought to use their services.
Today, as the crisis winds down, many multinational service providers operating in the region are again switching gears. Although many major consulting firms have cut back their restructuring operations and sent scores of foreign specialists home, other firms are expanding in Thailand by finding growing niche markets such as systems formulation, implementation and integration.
However, most professional service providers are in a state of flux.
During the past eight years, the booming US economy acted as the world’s growth engine. Today, with the US and European economic experiencing slowdowns, and the Japanese economy continuing to slumber, there are few external factors to drive small regional economies.
Closer to home, professional service providers are forced to adjust their operations as their clients prepare for an uncertain economic environment. During the boom times and the recent critical restructuring period, many large companies routinely hired professional service providers on a contractual basis when they needed them. If the firms wanted a specific problem studied and rectified, they would call in a professional service provider.
Today, major multinational companies as well as Thai companies are no longer satisfied with this type of arrangement. “These companies are now demanding a higher level of service,” said Edwin Sim, managing director and country manager Korn Ferry Thailand .
Major Thai companies that have virtually completed their restructuring processes are now looking at how they can best implement their new strategies and visions during this time of uncertainty, Sim said. “They are now demanding that service providers give them continuous consultative services.”
Companies that managed to survive the economic crisis are no longer comfortable calling service providers just to handle emergencies. “In a more uncertain economy, no CEO wants to fight unnecessary fires, which can be prevented with solid strategic planning and incisive policy implementation,” he said.
For the previously transaction-oriented service providers, the adjustment from transaction-based services to relationship-based services will mean new challenges. However, service providers such as lawyers, accountants, executive recruiters and other management consultants can invariably create a win-win situation for themselves as well as their clients.
In the long run, the service providers will be able to spread client acquisition costs over a customer base that uses more of their products and services. Clients benefit because they experience a more hands-on partnership with their trusted service providers. Rather than fighting fires when problems arise, the service providers are constantly available because under a retainer, they are continuously advising senior management during critical strategic policy formulation and implementation activities.
